Recent Posts
- A Guide To OTP SMS For Businesses
- What You Should Know About Mortgages, Restart Loans and Refinancing
- Why A Charcuterie Board Is A Perfect Gift
- Which Travel Kit is Right For You?
- Solo Traveler Tips For Getting the Most Out of Your Trip
- How to Finance My Mortgage
- What Are the Best Phones to Buy?
- The Best Computer For Games
- Beginner Diving in Socorro Island, Philippines
- The Basics of Scuba Diving in Australia
- Scuba Diving and Underwater Photography – The Best Snorkling in North America
- How Do Real Estate Prices Affect Your Community?
- Advantages of Hiring an SEO Service
- How SEO Tools Can Help Improve Your Website’s SEO
- How Do I Finance My Home Renovation?
- How to Finance My Mortgage
- Asian Dating Sites
- The Benefits of Dating a Younger Woman
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | ||||
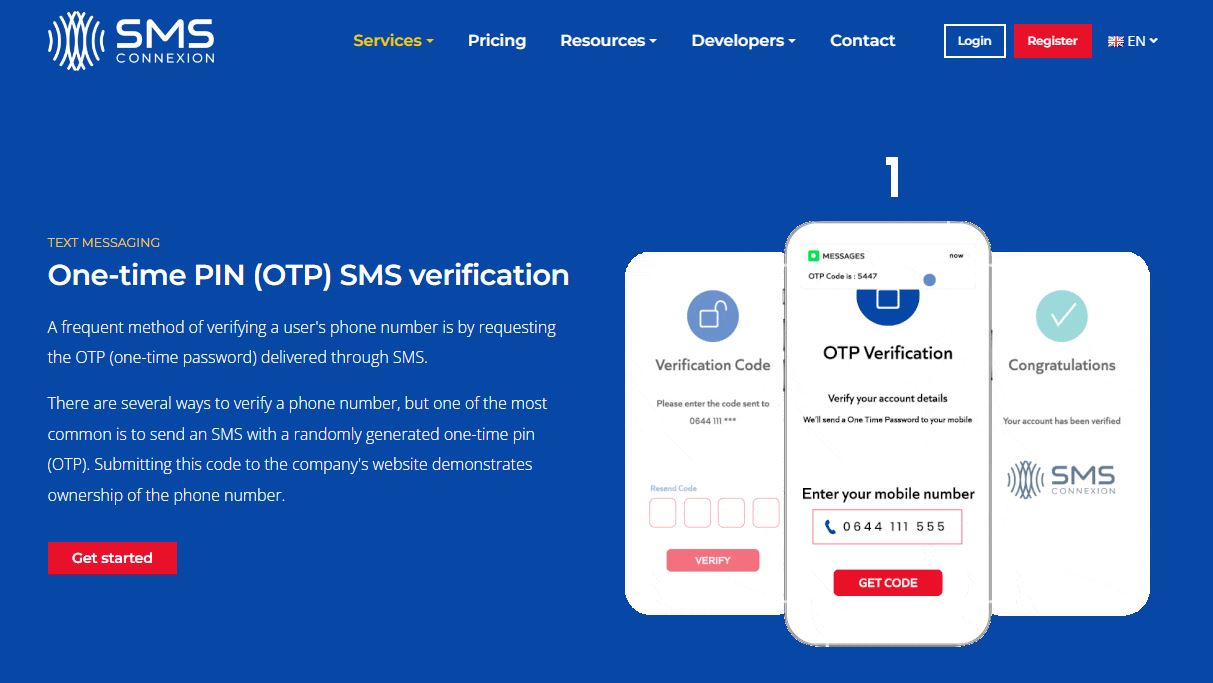
A Guide To OTP SMS For Businesses is a comprehensive guide to all of the different aspects of the OTP sms service. Whether you’re looking for the basic features of this service, or you want to find the most secure way to use it, this article will help you make the right decision. If you are looking for a trusted otp sms then ICSVA recommends SMS Connexions.
Security risks
SMS OTPs, or one time passwords, are used to verify and log into online applications and websites. They are also used by fraudsters to gain access to users’ accounts. However, they are vulnerable to many security risks.
The SS7 protocol has a flaw that allows hackers to intercept and read SMS messages. This is particularly dangerous because it compromises the confidentiality of SMS messaging.
There are a number of threats to SMS messaging, including attacks against cellular networks, malicious apps, and social engineering. These threats increase the risk of an account takeover.
For example, malware can monitor text messages on a compromised phone and use them to gain unauthorized access. Social engineering techniques can also be used to gain access to usernames and passwords.
Another common security threat is phishing. Fraudsters pose as legitimate organizations to trick users into providing their OTPs. A phishing attack is as dangerous on mobile devices as on desktop computers. To protect against this type of attack, it is important to educate users about how to avoid phishing scams.
JSON API vs SMS OTP
SMS is an encrypted text message that is used for two-factor authentication. Using this method, you can send a special code to the recipient’s phone to verify their identity. The code can also be used to access a remote device or secure sensitive data.
Getting started with SMS OTP is easy. You can opt for an off-the-shelf solution or build your own system. In either case, you’ll need to create an SMS DR endpoint, which will receive requests from the Orange server. Once your endpoint is set up, you’ll need to test it with real messages.
Getting the most out of your SMS DR endpoint is as simple as experimenting with different settings. You may want to consider setting a max timeout for sending SMS, which can range from 3600 seconds to 86400 seconds. This is important because you’ll need to wait at least fifteen seconds for an authentication request to complete.
As you may have guessed, the most obvious use for the SMMP access is to send and receive SMS. There are a few ways to do this, including using the SMPP access protocol, which is similar to REST.
Mogli SMS compliance checklist
It is important for SMS marketers to understand and follow the rules of the TCPA. Otherwise, they risk fines of $500 to $1,500 per incident. These penalties are intended to protect the consumer from being harmed by text messaging.
The TCPA is a federal law that governs the practices of businesses. In addition, the National Do Not Call Registry also applies to SMS marketing. Failure to follow these guidelines can cause a business to lose customers and revenue.
The CTIA, the Cellular Telecommunications Industry Association, has established a compliance checklist for SMS mobile marketing. This checklist will help you to ensure your compliance with TCPA regulations.
The TCPA requires you to get express written consent from consumers before sending commercial messages. You must also include a conspicuous disclosure and opt-out instructions in your commercial SMS messages.
Text messaging can be a valuable tool for businesses, but if you don’t follow the TCPA and other laws, you could face costly fines and lawsuits. Luckily, there is a simple and easy-to-follow SMS compliance checklist that can help you stay compliant.
SMS scams soared by 328% in 2020
A report from Proofpoint showed that smishing attacks grew 328% in the third quarter of 2020. Smishing is a form of mobile-based phishing. This type of phishing involves the use of text messages to distribute malware and spyware. The links provided by the attackers often lead to unsafe websites. When users click on these links, the attackers gain remote access to the victims’ devices and keystrokes, as well as access to their screens. These threats can lead to identity theft and potential fraud.
In March of 2020, a smishing campaign was detected in South Africa. It was aimed at impersonating a local financial institution. It warned recipients that their account would be terminated if they did not provide certain bank details to confirm their eligibility for a vaccine. Thousands of people clicked on the malicious links, which led them to the same website. One man was sentenced to four years and three months in prison for his role in the smishing scheme.